Procedure
Sample Report
A qualitative report is essential for every penetration test. Comprehensive descriptions on the technical and management level give a clear understanding of all vulnerabilities.
Management Summary
Our final report includes a non-technical summary of the project and all identified findings for the management level. All findings are summarized concisely.
Approach, Scope and Tools
Furthermore, our final report includes a detailed description of our testing methodology, the analysed test target, scope and used tooling.
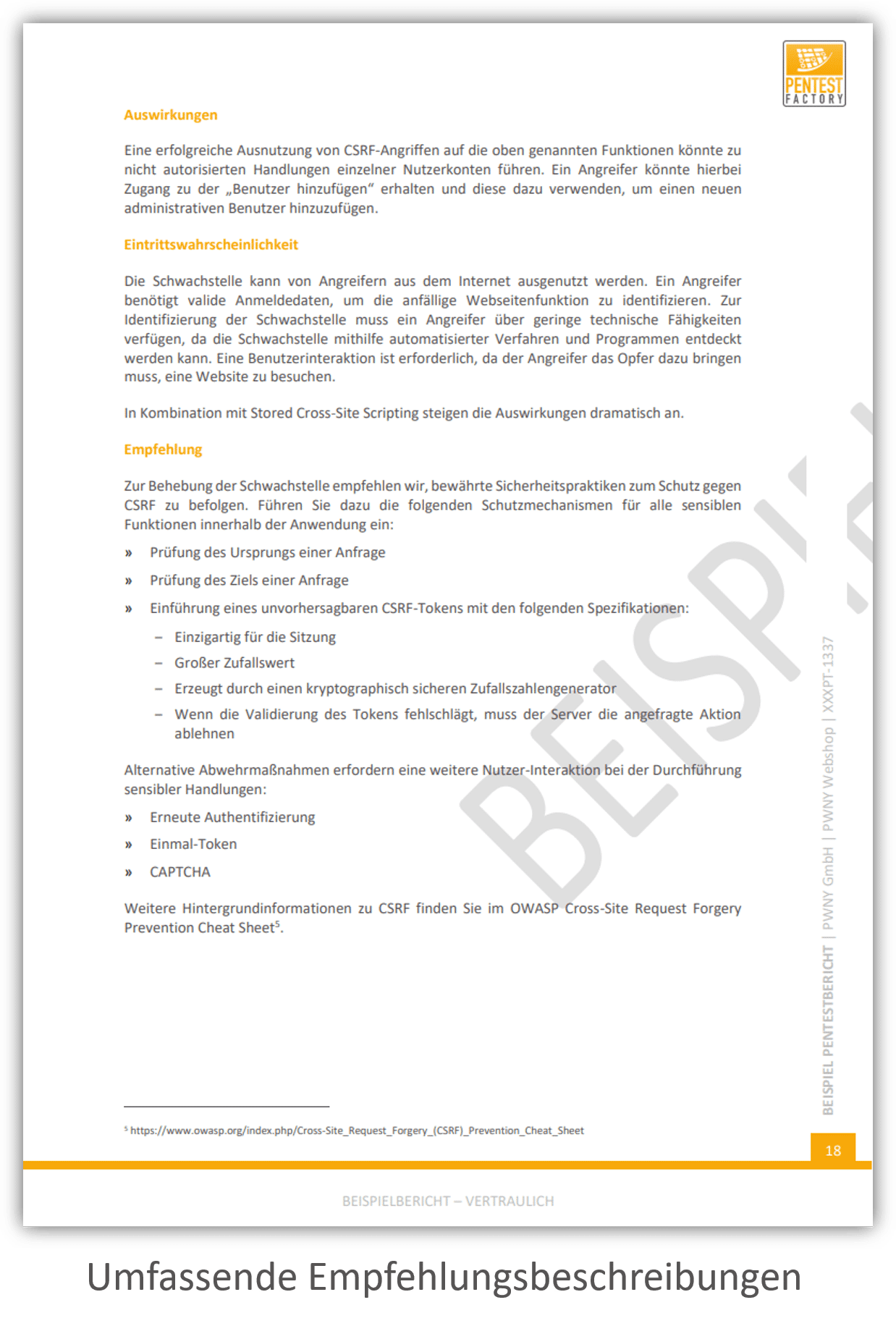
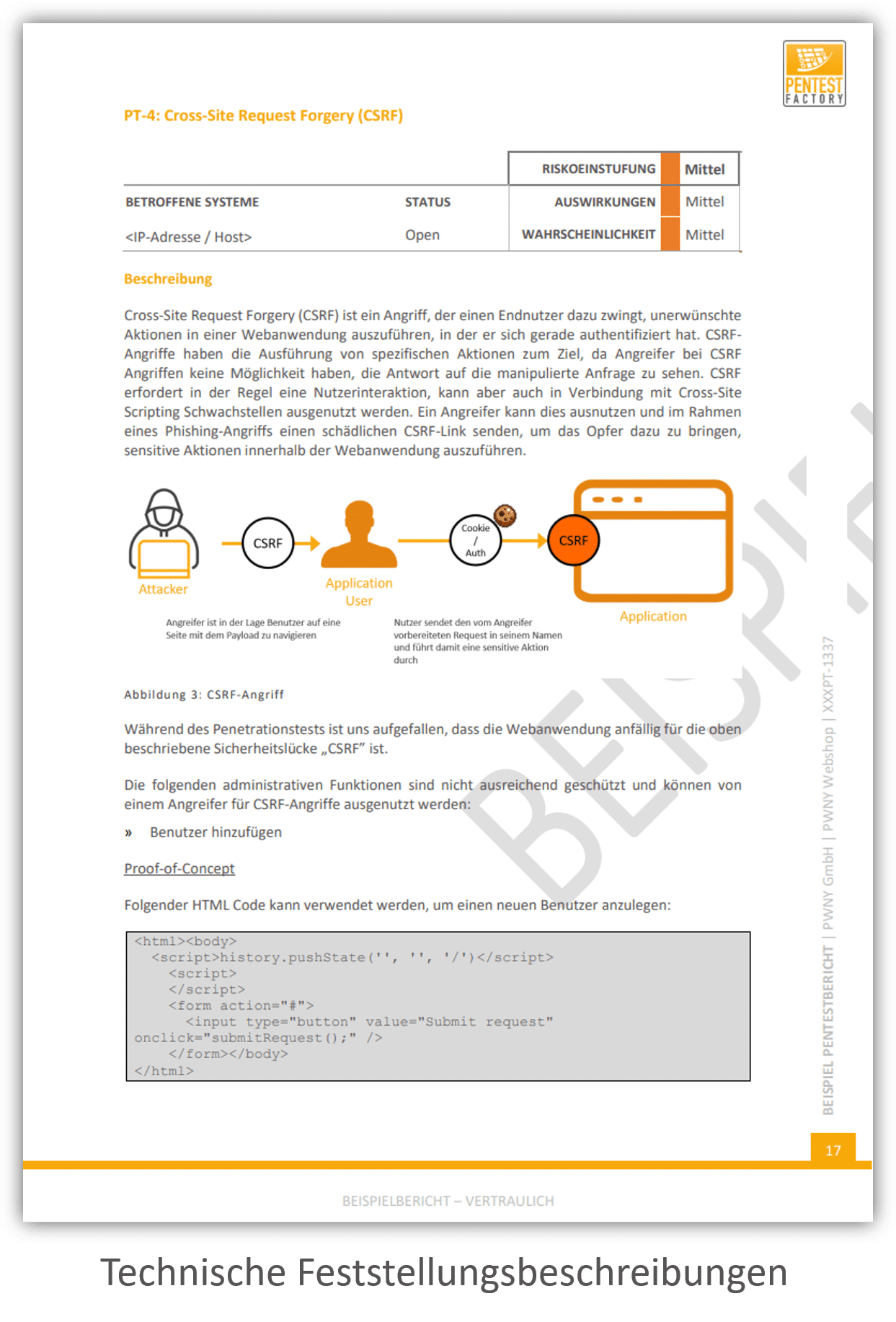
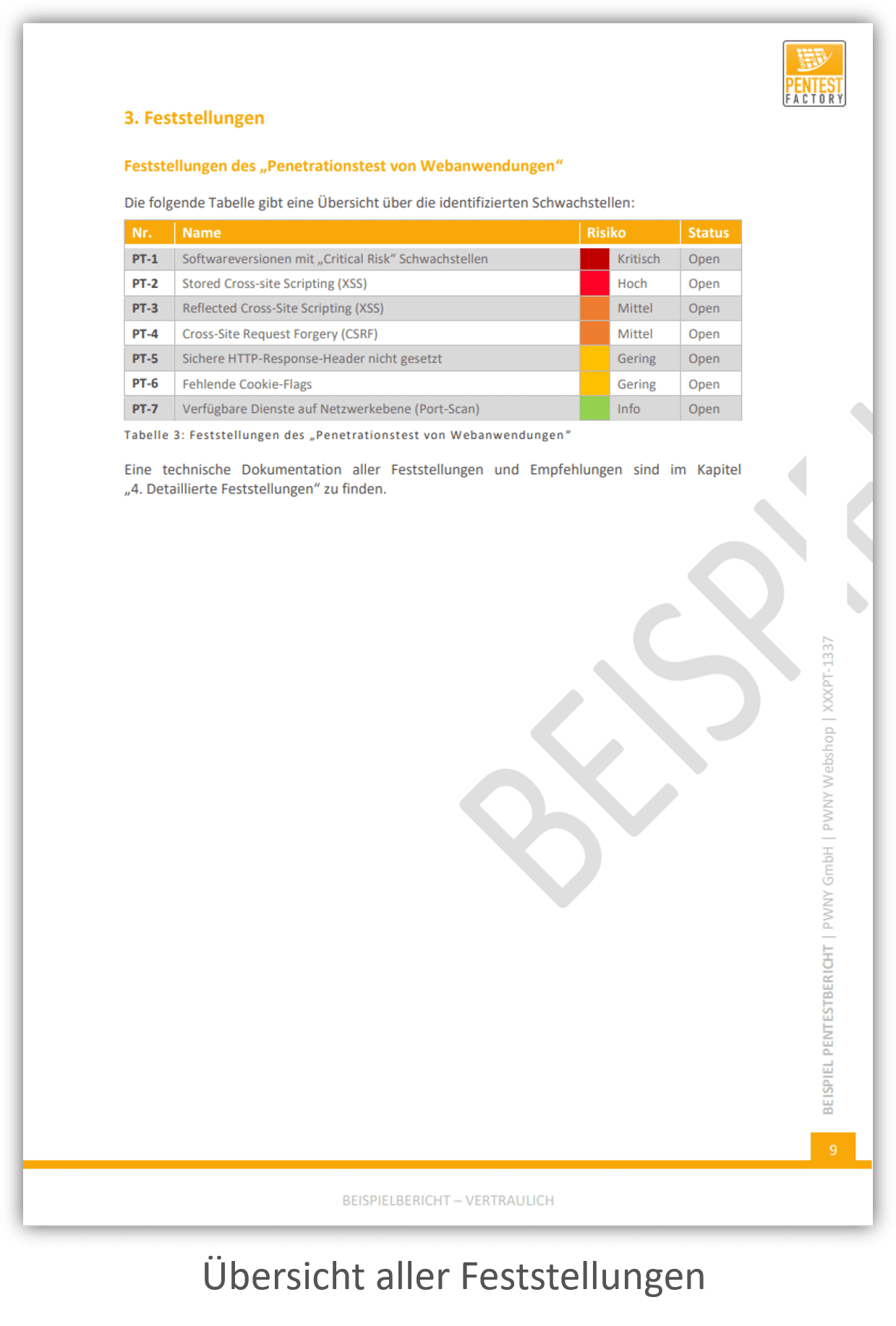
Findings and Recommendations
In addition, our final report contains a detailed, technical description of all identified findings. You receive a detailed recommendation for the remediation of every vulnerability. This aids technical personnel, such as administrators or developers.
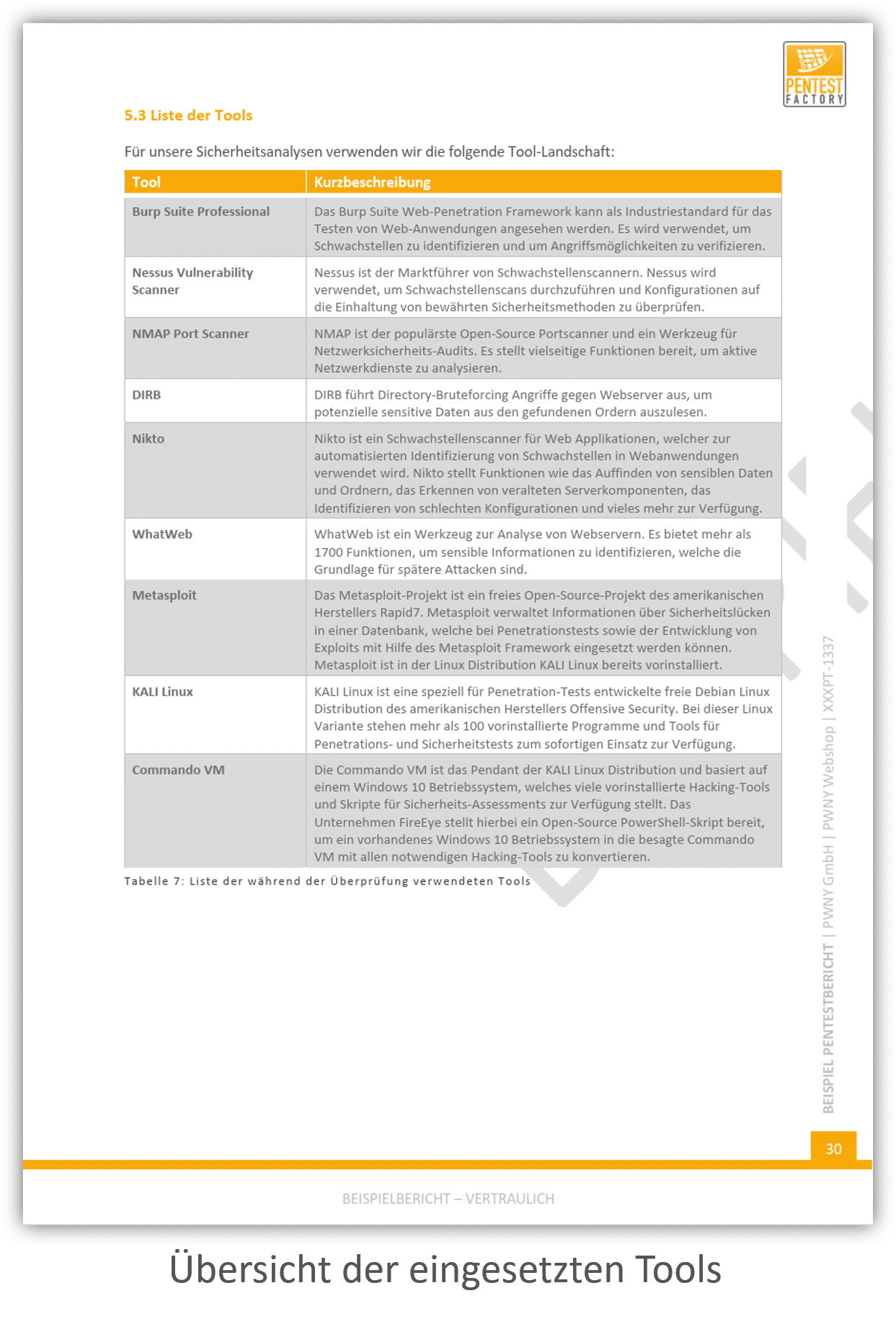
Standardized Risk Rating
We adhere to recognized standards like the OWASP risk rating procedure for the scoring of identified vulnerabilities. The risk of a vulnerability is based on its likelihood and impact.





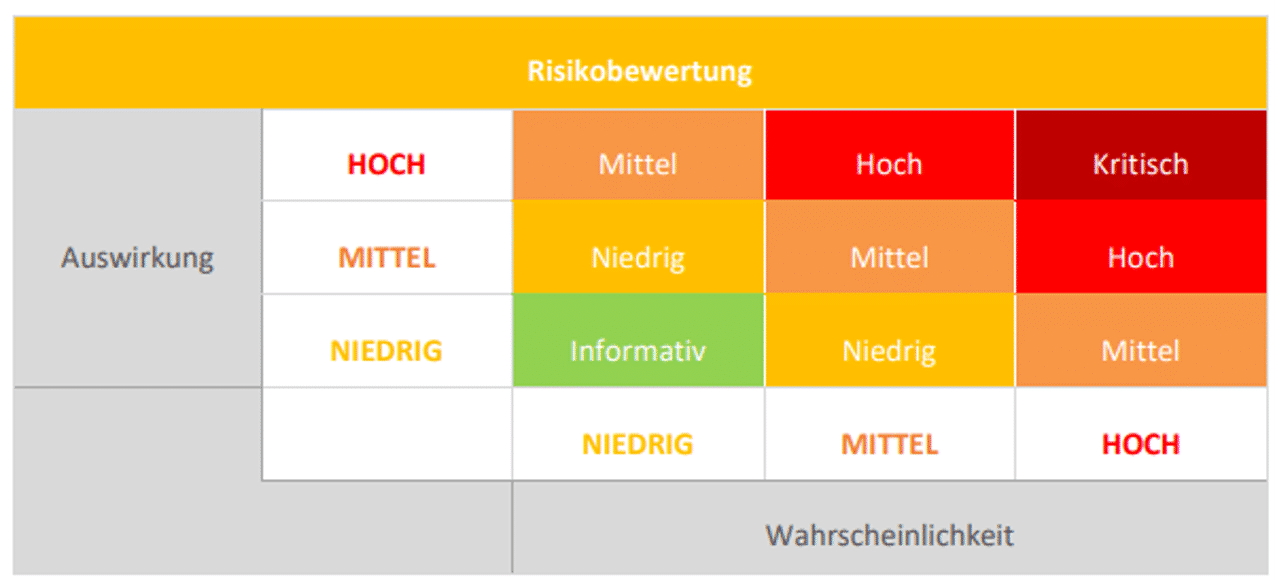
OWASP Risk Rating Procedure
The risk rating is assigned following the OWASP risk rating procedure, which is based on the factors probability and impact. In the following, our risk rating matrix can be seen:
These vulnerabilities can be abused by attackers with low technical knowledge using publicly available exploits.
Vulnerabilities that can be exploited manually by an attacker. No publicly known exploits exist.
Vulnerabilities that allow an attacker to access sensitive functions or information. The privileges an attacker can obtain through exploitation of these vulnerabilities is limited.
Vulnerabilities, which do not pose an immediate risk, but may serve as a platform for further attacks.
Useful information that might indicate potential errors. These findings do not constitute a security risk, but should be evaluated.
Optionally, we offer a risk rating procedure using CVSS v3. More Information can be found in the CVSS specification.
