Dealing with vulnerabilities in IT environments is more important than ever. The media publishes daily articles about new vulnerabilities being discovered, published or exploited. We have now released our own vulnerability database for the public and allow all users to search the database for vulnerability reports and entries.
We have detailed the technical background and implementation of this database in a separate article “CVE Quick Search: Implementing our own vulnerability database“. Now the database is ready and we have made access public. All visitors of our website can use the query form freely.
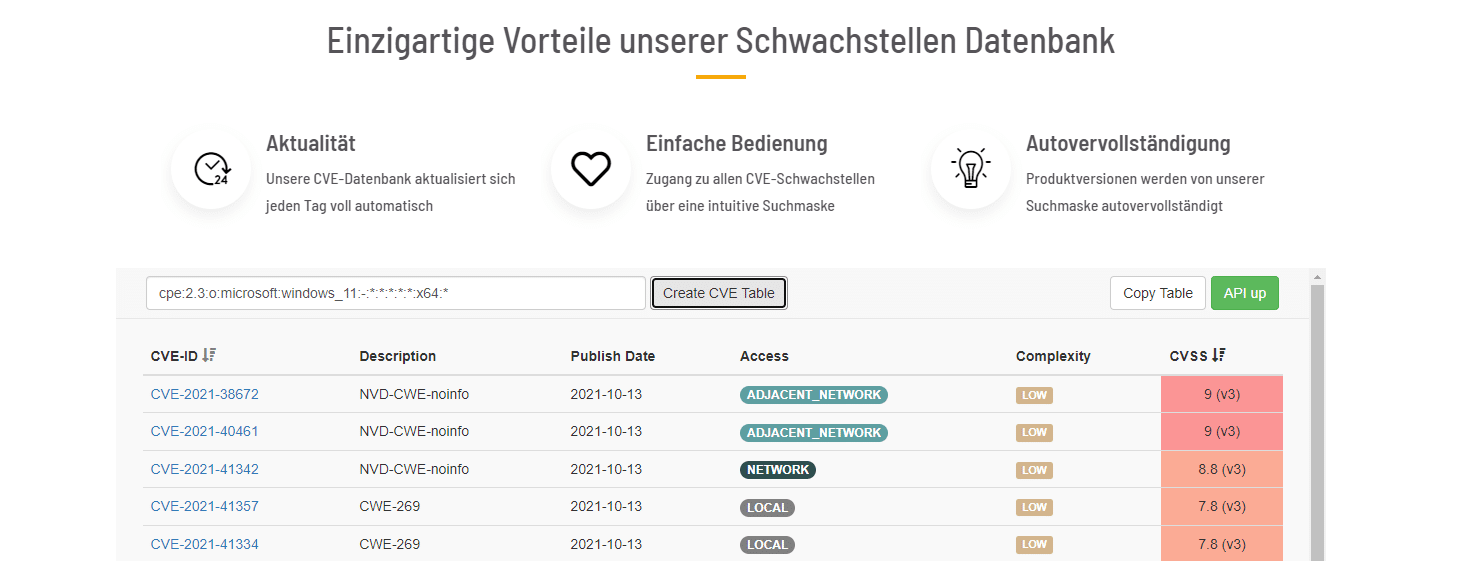
Accessing the database is plain and simple. Enter the software name and version into the search field. The system suggests matching product entries via an auto-complete mechanism. After choosing the right entry, click on “Create CVE Table” to generate a table that lists all known vulnerabilities for the chosen version. The table is sorted by criticality (CVSS Score). Using the “Copy Table” button, you can copy the found entries and e.g., paste them into your presentation.
We gladly support you in creating an efficient vulnerability management concept for your company. Feel free to contact our specialists and receive more information without committment.

